By default, Apache stores all logs to the local disk. This works well for development environments and small deployments, but becomes unsustainable once you have more than one server. Not only is it frustrating having to open each log file on each server, but trying to trace requests across multiple servers can quickly become time-consuming.
A MAC address is an integral, unchanging element of any hardware device. It’s a good way to keep track of the devices on your network. With a MAC address finder, you can enter the MAC address of a device and the tool will locate that device and gather other pertinent information, including its IP address. Kiwi Syslog Server Free Edition by SolarWinds (FREE DOWNLOAD) Kiwi Syslog Server. Jun 13, 2021 It runs on Windows, Linux, Mac, FreeBSD and Solaris. SoftEther VPN is open source. You can use SoftEther for any personal or commercial use for free charge. SoftEther VPN is an optimum alternative to OpenVPN and Microsoft’s VPN servers. SoftEther VPN has a clone-function of OpenVPN Server. You can integrate from OpenVPN to SoftEther VPN smoothly. SolarWinds Kiwi Syslog Server. Kiwi is a SolarWinds product, so you know it is good.
Log centralization services prevent this by allowing you to store logs from your Apache servers in a single location. This makes it possible to view all of your web logs without having to open each log file individually. Many log centralization services can also automatically parse your logs, and provide a user interface that lets you scroll, search, and filter through your log data in near real time.
This section shows different methods of aggregating and centralizing logs from your Apache servers.
Syslog
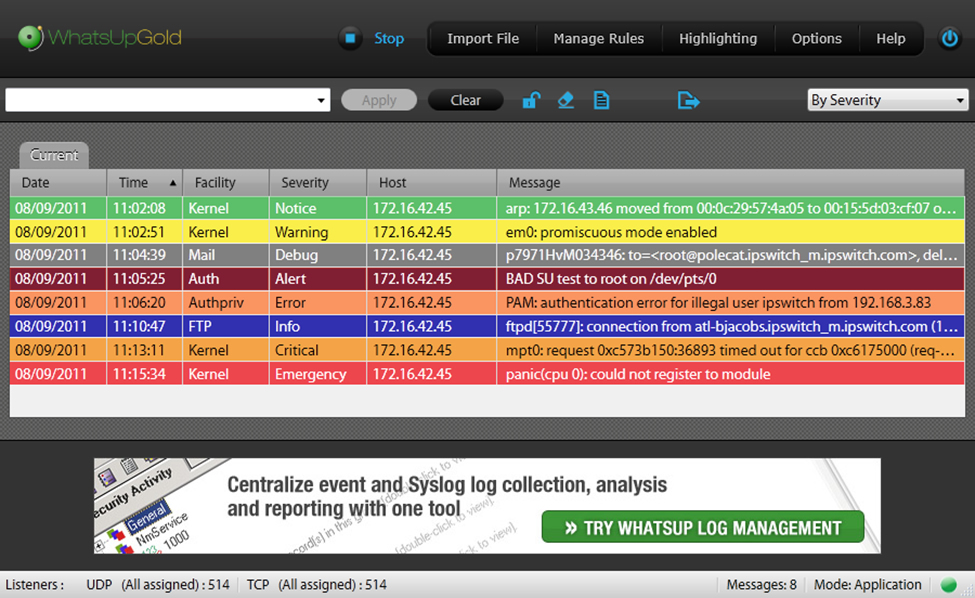
Syslog is a logging service commonly found on Linux, Unix, and Mac systems. Syslog handles logs from a number of different sources including applications, system services, daemons, and hardware. Syslog is reliable, standardized, and can even forward your logs to another syslog server.
A common approach to reading Apache logs is to configure syslog with file monitoring. With file monitoring enabled, syslog periodically scans a file on the system for changes, then imports those changes into its own log file. The benefit is you get the complete original log message wrapped in the standard syslog message format without modifying the original file.
Configuring File Monitoring in Syslog
The most common way to enable file monitoring is by installing and configuring rsyslog. rsyslog is a complete syslog server with file monitoring built in. It’s easy to configure, fast, and supports log rotation, which is commonly found in Linux distributions such as Ubuntu.
The following rsyslog configuration monitors both the Apache access and error logs. You may need to replace the file names depending on your configuration.
Save this to your rsyslog configuration file, then restart the rsyslog service.
Some vendors have scripts or agents that will configure rsyslog to monitor these log files, making setup easier. For example, SolarWinds® Loggly® built a script that will automatically configure rsyslog to monitor your Apache logs.
Filtering Logs Before Centralization
In some situations, you may want to filter your logs before sending them to your centralization service. For example, you may only want to send error codes in order to use less storage on the remote system. With rsyslog, we can add a condition to our file monitoring rule that only allows events containing certain HTTP status codes.
This configuration example drops all messages where the status code is not 500 or 502. stop tells rsyslog to discard the message.
Piping to Logger
Apache doesn’t just support logging to files. For example, you can also send logs directly to a syslog service using a custom logging pipeline. The most common method is to use the /usr/bin/logger command, which forwards logs over a syslog socket to the syslog service. This lets you bypass the file monitoring process, which could have performance advantages on slower storage devices. In addition, you no longer have to store a separate log file for Apache.

The downside to this approach is it removes the local backup provided by your Apache logs. If there’s a problem sending your logs from logger to syslog, you could lose messages. In addition, logger supports a maximum message size of 1024 bytes. However, you can increase the size of this by adding the --size parameter.
To set up a logging pipe, open your Apache configuration file and replace your logging configuration with the following.
Splunk Forwarder Mac
Restart the Apache service to apply the changes.
Now your logs will no longer be written to the access.log and error.log files, but will instead go straight to syslog. If you want to continue logging to file as well as syslog, you can use the following configuration instead. This uses the tee command to first pipe the log message to file, then pipes the output from that command to logger:
See it. Analyze it. Inspect it. Solve it
See what matters.
START FREE TRIALSyslog Configuration
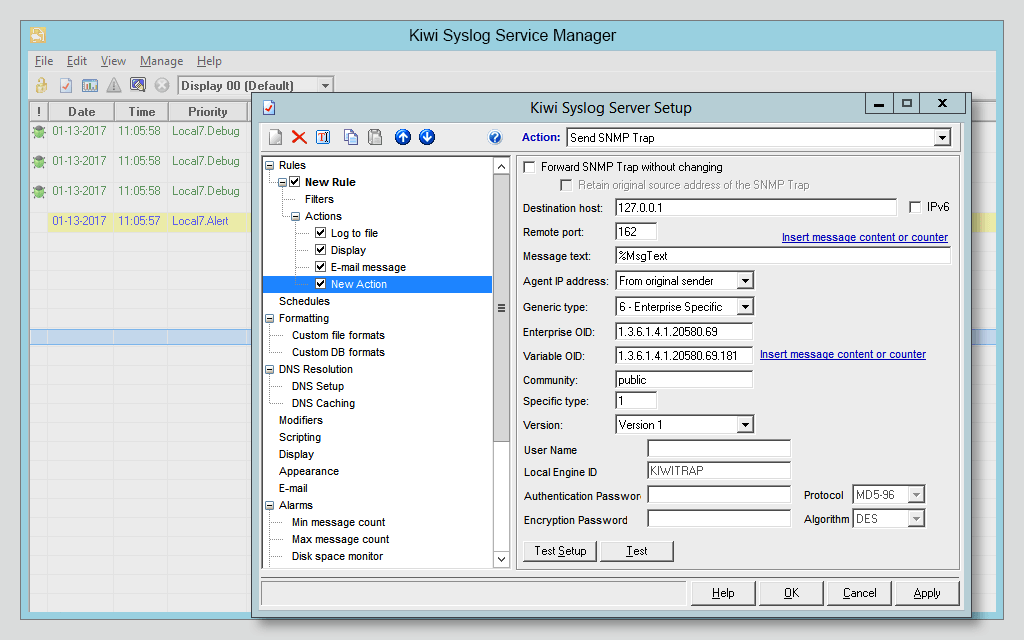
A syslog server can be configured to store messages for reporting purposes from MX security appliances, MR access points, and MS switches. The MX Security Appliance supports sending four categories of messages/roles: Event Log, IDS Alerts, URLs, and Flows. MR access points can send the same roles with the exception of IDS alerts. MS switches currently only support Event Log messages.
To begin setting up a Syslog server on the Meraki dashboard, first, navigate to Network-Wide > Configure > General. Here you will see a section for Reporting, with the option for Syslog server configurations. Click on the Add a syslog server link to define a new server. Configure an IP address of your syslog server, the UDP port the server is listening on, and the roles you wish to be reported to the server.
If the Flows role is enabled for Meraki MX reporting, logging for individual firewall rules can be enabled/disabled on the Security appliance > Configure > Firewall page, under the Logging column as shown below:
Additional Considerations for Syslog
Storage Allocation

Syslog messages can take up a large amount of disk space, especially when collecting flows. When deciding on a host to run the syslog server, make sure to have enough storage space on the host to hold the logs. Consult the syslog-ng man page for further information on only keeping logs for a certain amount of time.
Expected Traffic Flow
Syslog traffic may flow to the syslog in one of three scenarios depending on the route type that is used to reach the syslog server. Below are example scenarios and a detailing of expected traffic behavior.
Scenario 1 - Reachable via LAN
The MX will source traffic from the VLAN interface that the server resides in if the syslog server is located on the LAN of the MX. The transit VLAN interface would be used if the device is only accessible via static route.
Scenario 2 - Reachable via Public Interface
The MX will source traffic from the public interface (WAN) if the syslog server is accessible via the WAN link.
Scenario 3 - Reachable via AutoVPN
The MX will source traffic from the interface of the highest VLAN that is participating in AutoVPN if the syslog server is accessible via AutoVPN.
Syslog Server Software
If the traffic passes through the site-to-site AutoVPN connection the traffic will then be subject to the 'Site-to-site outbound firewall' rules and as such an allow rule may be required. This can be configured in Security appliance > Configure > Site-to-site VPN > Organization-wide settings > Add a rule as shown below.